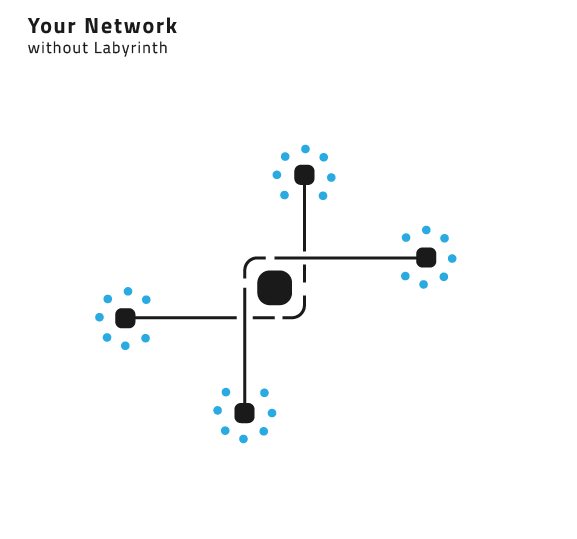
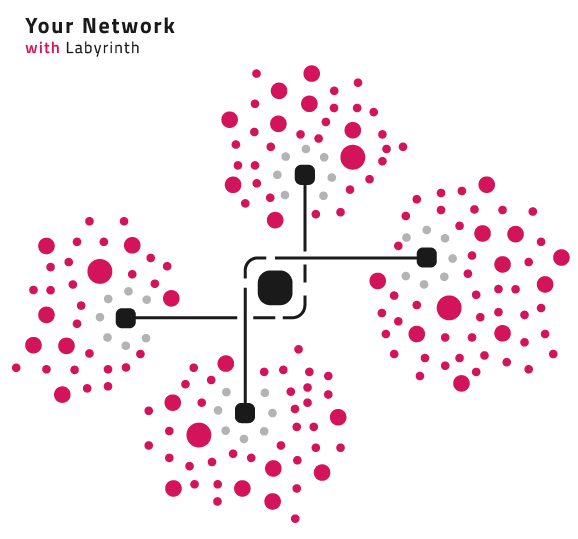
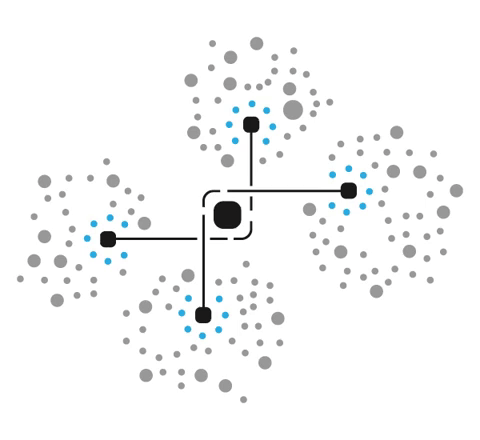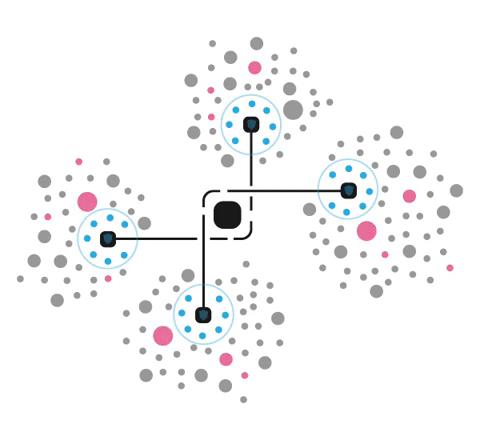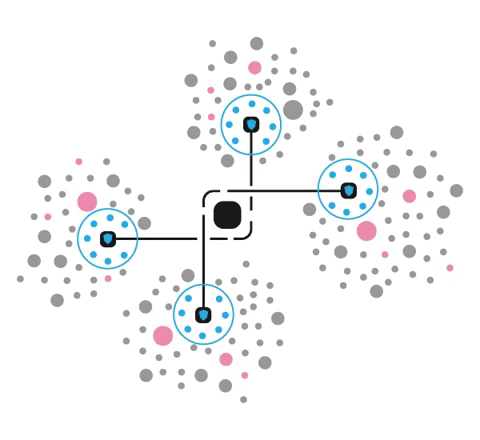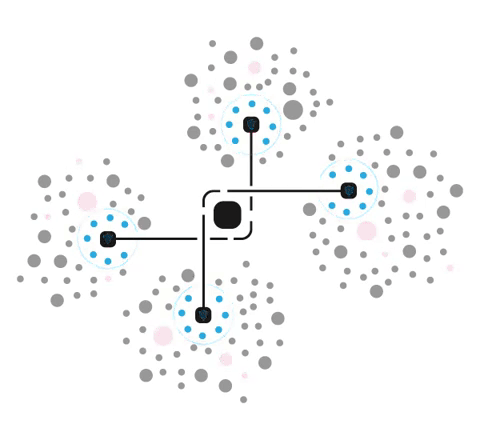
Cybertrap is a combination of technologies built to detect, identify, and eliminate cyber threats while turning your network into a complex labyrinth full of deceptive but highly realistic workstations and applications.
go ahead,
Activate Labyrinth

Our product is designed to slow down, confuse, and trap attackers while your response team makes sure that the threat is cornered and dealt with safely. Cybertrap turns cyber predators into prey by luring them into tens, hundreds, or even thousands of illusory workstations and servers that are spread throughout your entire network.
Our product is designed to slow down, confuse, and trap attackers while your response team makes sure that the threat is cornered and dealt with safely. Cybertrap turns cyber predators into prey by luring them into tens, hundreds, or even thousands of illusory workstations and servers that are spread throughout your entire network.